Taking action to fix your Google Chrome browser could be the catalyst that infects your PC with malware. Millions of users have been warned by new research.
Experts from cybersecurity firm Proofpoint have discovered a dangerous campaign that masquerades as a fake update in your Google Chrome web browser to force you to download malicious code. Following the steps described in the fraudulent pop-up will unleash a Trojan horse-like attack on your PC.
Hackers can then search the personal data stored on your desktop PC or laptop, the researchers outline a detailed blog post about the newly discovered attack.
Security experts have discovered a few examples of fraudulent Google Chrome pop-ups that encourage web browser users to paste malicious code into a terminal window on their computer
EVIDENCE POINT
Worse still, malicious software could be deployed to divert cryptocurrency sent from your PC into hackers’ pockets, security experts have warned. Proofpoint researchers have not revealed how much money they believe was stolen from PC owners worldwide using this technique.
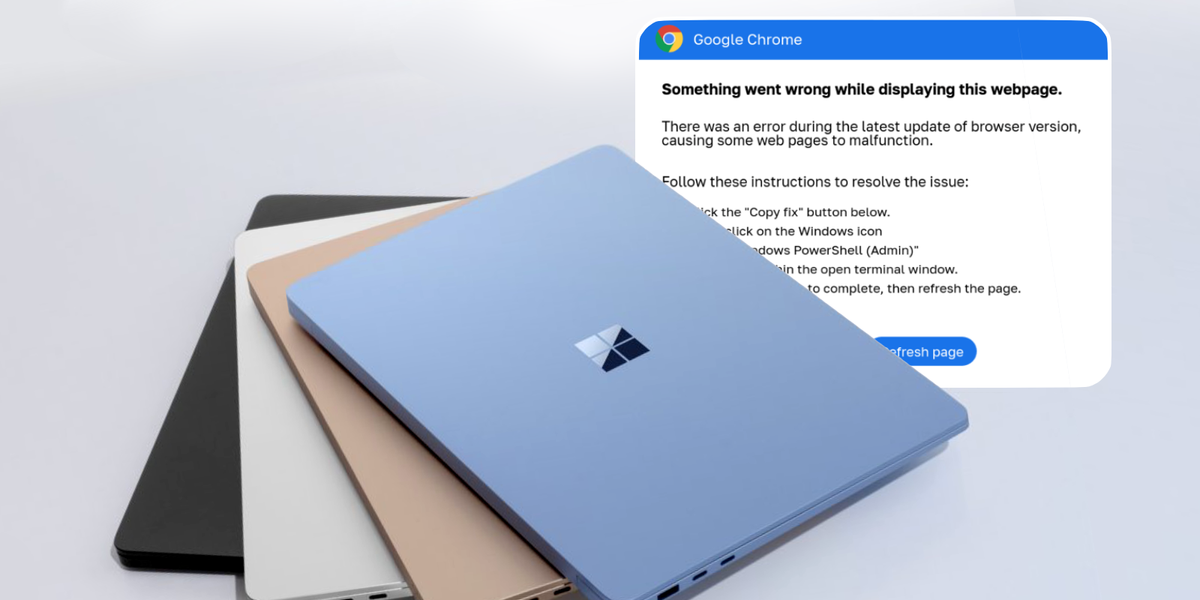
“Aw, Snap! Something went wrong while displaying this web page,” reads an example of the fraudulent pop-up message discovered by security experts. “To display this web page correctly, please install the root certificate. Click the ‘Fix it’ button and follow the further instructions.”
Another reads: “Something went wrong while displaying this web page. An error occurred during the last browser version update that caused some web pages to not function properly.”
Both fraudulent pop-ups encourage users to copy the malware code with one-click, launch Windows Powershell (Admin) – a pre-installed app that allows users to control and automate parts of the operating system – from the Start menu, the malicious code and run it in the terminal window.
In other words, it’s a step-by-step guide that teaches Windows users how to perform the attack themselves.
This technique of using “fake error messages,” the researchers warned, “is clever and purports to be an authoritative message coming from the operating system.”
Any person or application that instructs you to execute unknown code within a terminal or shell should set off alarm bells, researchers advised. This deep level of system access allows hackers to cause enormous damage.
And it’s not just Google Chrome users who need to be wary of these types of attacks. Proofpoint researchers have discovered evidence of a very similar attack targeting Microsoft Word users.
The malicious pop-up is designed to look like a legitimate warning from Microsoft and – like the attack targeting Google Chrome users – will trick unsuspecting users into pasting code into a terminal.
“The ‘Word Online’ extension is not installed in your browser. To view the document offline, click the ‘How to fix it’ button,” reads an example of these fraudulent alerts.
Although the browser-based version of Microsoft Word works on all platforms, the hack is specifically designed for the Windows operating system. As such, only those running Windows 10 or Windows 11 will be affected by hackers’ latest campaign.

Another example of this type of attack, highlighted by Proofpoint researchers, targets people using Microsoft Word in their browser
EVIDENCE POINT
Researchers point out that this attack “requires significant user interaction to be successful,” which could limit its impact globally. Proofpoint researchers add: “Organizations should train users to identify the activity and report suspicious activity to their security teams.
“This is very specific training, but can easily be integrated into an existing user training program.”
LATEST DEVELOPMENTS
Applications will be Google Chrome and Microsoft Word never ask you to manually enter code into another application to unlock features. If any of the above pop-up warnings (or similar instructions) appear on your PC, exercise extreme caution.